When deploying into the enterprise environment, there’s a lot of flexibility when it comes to deciding how you structure the deployment, whether you want to run supporting services on-premise, and which ones (if any) you choose to deploy. The decisions depend on how you plan to use our software and your security requirements. We’ll be glad to assist you during this process. Please contact us at human@flowcrypt.com.
Full deployment diagram
Below is a diagram depicting the overall architecture when deploying on-premise:
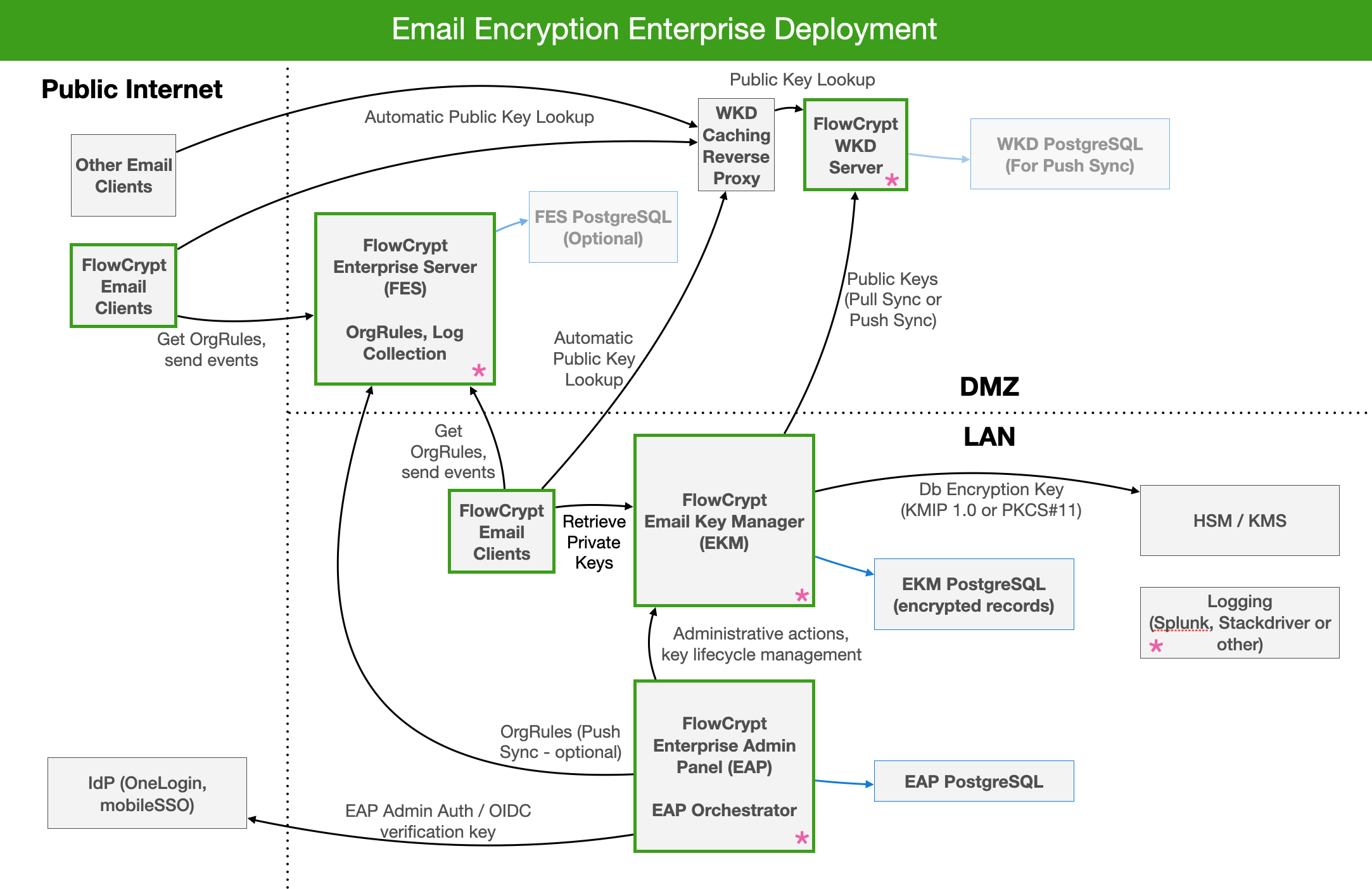
This suits large enterprises that require automation, full control, recovery, and auditing capabilities.
FlowCrypt provided products
In this table, you see FlowCrypt products that are green-bordered in the diagram above:
| Product | Deployment | Purpose |
|---|---|---|
| Email Clients | Required | Our browser extension. Alternatively, our Android or iOS apps. |
| Email Key Manager (EKM) | Optional | Stores and serves user private keys centrally within the local LAN. Alternatively, you can opt to manage keys manually or through the existing solution. |
| Web Key Directory (WKD) | Optional | Serves public keys to external users for automatic encryption between organizations. |
| Enterprise Admin Panel (EAP) + Orchestrator | Optional |
Enterprise Admin Panel allows your privileged users to do administrative actions regarding key management and distribution. EAP Orchestrator handles key lifecycle actions like automatic key expiration, renewal, and rotation. |
| External Service (FES) | Optional | Accounts and configuration service for the Email Clients to retrieve Client Configuration, send logs, and provide other accounts functionality. You can either deploy an enterprise FES server or use a shared-tenant solution hosted by us. |
All server-side services are optional. You can deploy standalone email clients for the easiest/fastest deployment.
Your optional infrastructure
When deploying an enterprise-server, our services may interact with your existing infrastructure for tighter integration.
| Service | Purpose |
|---|---|
| Identity Provider (IdP) | Your existing identity provider for unified user authentication (Single sign-on (SSO) such as OneLogin, Auth0, or others). You can optionally use Google as an identity provider. |
| Logging | Your existing logging and events infrastructure such as Splunk, Stackdriver, or others. Optionally, you can simply log to stdout or to a local file. |
| Hardware Security Module (HSM) / Key Management Service (KMS) | Your existing secure key storage solution such as HSM / KMS products from Gemalto, Fortranix, Atos, Thales, or others. |