On this page, you’ll find a group of questions that are less common.
How to view a message in its original form without FlowCrypt?
I want to be able able to break out of FlowCrypt on the fly, so I can fall back to normal Gmail compose if needed.
As it is, I appear to be forced into the FlowCrypt Secure Compose when responding with contacts that could use OpenPGP.
In a conversation that was originally encrypted, you can click the See original green button on the top right.
There, you can also reply in the standard way without encryption.
Export a key from GPG Keychain/GPG Suite on a Mac
I’d like to export my key from GPG Suite on a Mac, what do I do?
If you want to re-use your key from GPG Keychain (which is a good idea), this is a way for getting the key out of it.
On your Mac, in the GPG Keychain app, select the key that says sec / pub in the Type column, then click Export on the top.
Select the ASCII format and save it into a file. Then, open the file in a text editor and you should see a lot of garbled-up text in it, starting with the following text:
-----BEGIN PGP PRIVATE KEY-----
Copy everything in that file and paste it where FlowCrypt asks for it during the setup process.
If you’ve already set up FlowCrypt without the key, you can still go to FlowCrypt Settings ⮕ Additional Settings ⮕ My Keys ⮕ Add key and add it there.
Password encrypted messages expiration - how does it work?
I want to know what exactly the following means: “Password-protected messages expire in X days”
Messages that you send to people who don’t use encryption on their end will require that you add a password to protect them.
Such messages will be encrypted on your end using the password, then stored in encrypted form on FlowCrypt servers to be delivered to the recipient.
Unfortunately, many people will use fairly weak passwords. Given enough time and resources, someone could crack the messages with brute force.
That’s why such messages expire. Once expired, they’ll not be served from our servers anymore, and within some period of expiration, we’ll delete them from our servers.
We expire and delete these emails within 90 days of sending for both free users and Enterprise users who use Shared Tenant FES. We do this to protect users who may have used a weak password.
Some use cases require that the message is available longer than the standard 90-day expiration. FlowCrypt Enterprise users who run their own server infrastructure can choose the expiration time.
Messages sent between people who use encryption don’t expire, because they are delivered over email like any other message, plus typically encrypted in a more secure way.
For more details and screenshots see the Send and Receive Encrypted Emails section.
“Manually importing public keys can be dangerous” - can you please explain?
Importing a public key, especially from an unknown source, can be dangerous. For example, you’ve received an email from a stranger that includes a public key, and you import it.
Importing the incorrect public key means your message will be encrypted for the wrong person, which is dangerous! As a result, received messages may appear to be signed by someone when in fact they’re not. This is also dangerous!
If you’re part of an enterprise that uses the Enterprise version of FlowCrypt, ask your internal Help Desk for guidance.
Otherwise, proceed with caution. It’s best to reach out to the sender by other means, for instance, via a telephone, and verify that they’ve indeed just sent you the public key and that the fingerprint of the received public key matches the fingerprint of the one they sent.
Uninstall FlowCrypt
You can remove the extension from Chrome, Brave, or Firefox. Right-click the icon in your browser and choose Remove from Chrome/Brave. Your browser stores Google access tokens locally and will remove them with the extension.
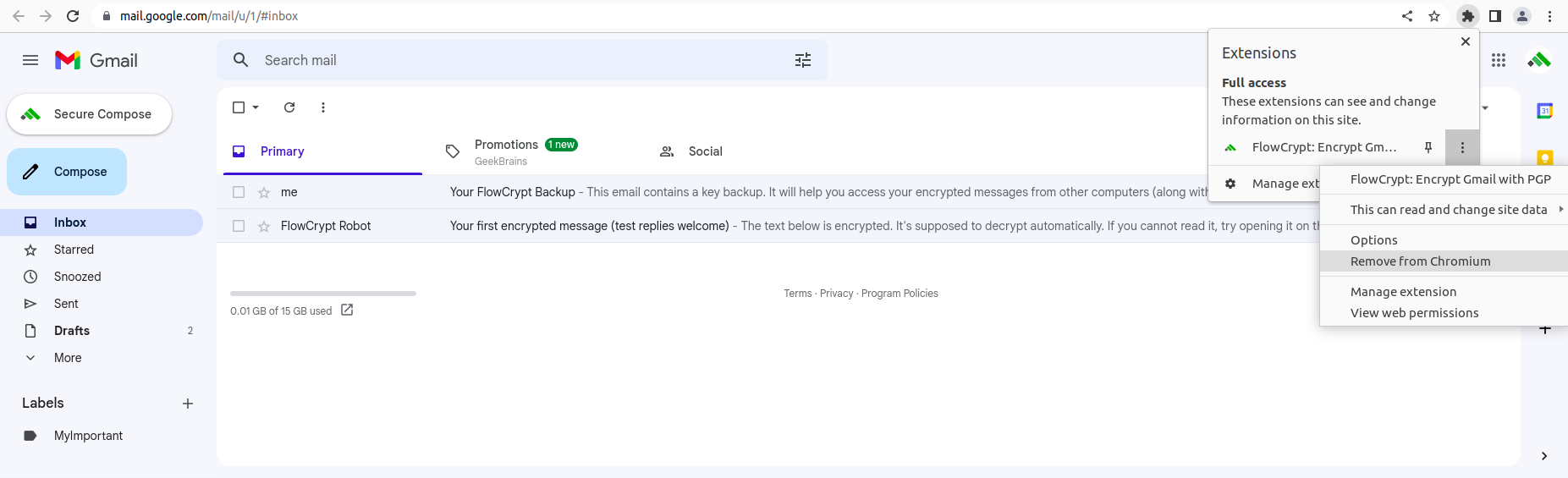
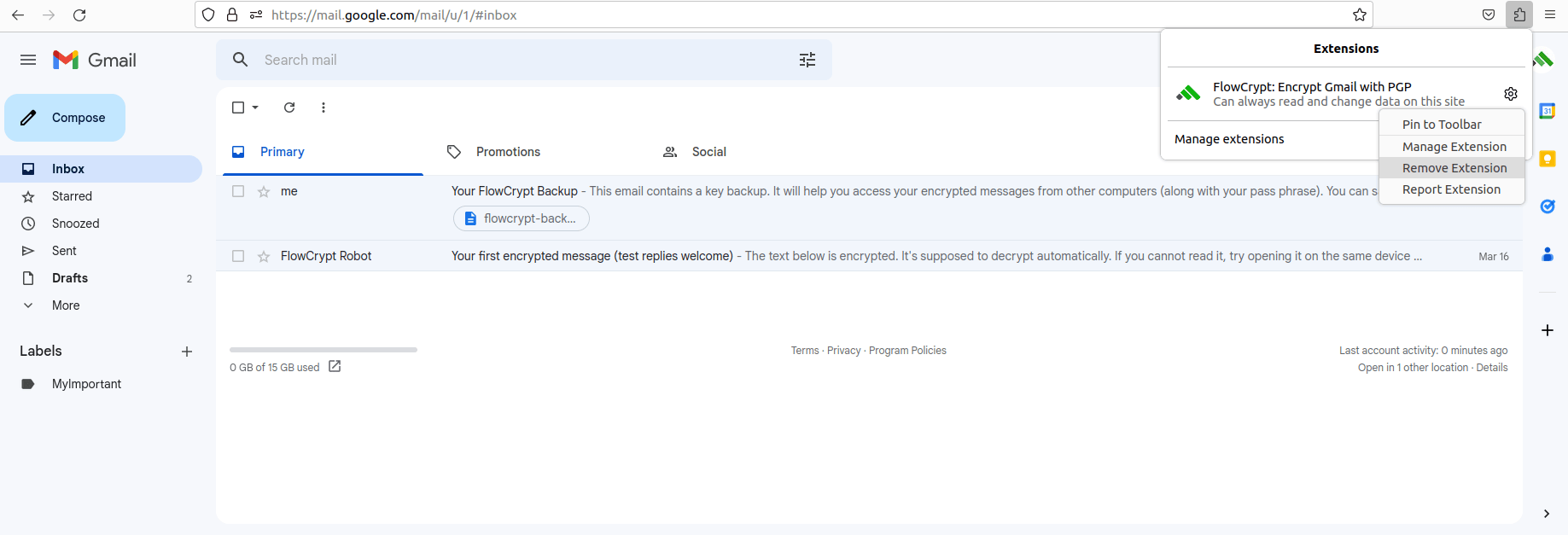
If you use Firefox, choose Remove Extension:
How to delete account
Google permission tokens are removed along with the app when you uninstall FlowCrypt. You can also revoke the access tokens at myaccount.google.com .
If you don’t plan to continue using encryption, you can hide your public key records .