This page explains the configuration options for the following two service components:
There may be cases when FlowCrypt users write to someone who hasn’t set up encryption or whose public key isn’t known. In such situations, they can send the message through the Web Portal, where the recipient can open and view it using a message password.
Properties file section: Web Portal
| Property | Description |
|---|---|
web.portal.url optional |
The base of the URL given to clients after a message upload occurs. Default value: https://fes.<org.id>Example: https://fes.evaluation.org
|
web.portal.replies.sender.email |
The from email header field when web portal replies are sent.Example: web.portal@evaluation.org
|
web.portal.pubkey.source.attester.enabled |
Whether to get public keys from FlowCrypt Attester, when replying from the Web Portal. In this scenario, the original sender of the message to which you’re replying, as well as possibly other correspondents, may have a public key to encrypt the message. If you’re running the Web Key Directory, whether separately or as a part of Enterprise Server, and you don’t expect to communicate this way with FlowCrypt users outside of your organization who have their public keys in FlowCrypt Attester, you can set this option to false. This means that all public keys will only come from your WKD.Example: true
|
web.portal.display.signature.warnings optional |
Set to true or false to enable/disable the display of the signature verification-related warning message on the FES encrypted message page.Default value: falseExample: true
|
web.portal.wrong.password.attempts.before.timeout optional |
The number of attempts after which security timeout is carried out. Default value: 5Example: 10
|
web.portal.wrong.password.timeout.seconds optional |
The duration of the security cooldown period in seconds. Default value: 300Example: 180
|
Opening web portal messages
To understand how recipients open password protected messages sent through the Web Portal, see the step by step guide here.
This guide explains the full recipient experience, including entering the message password and viewing any decrypted attachments.
Anti Brute Force options
To prevent brute force attacks, FlowCrypt implements an optional feature to set a maximum number of password input attempts and a security cooldown period.
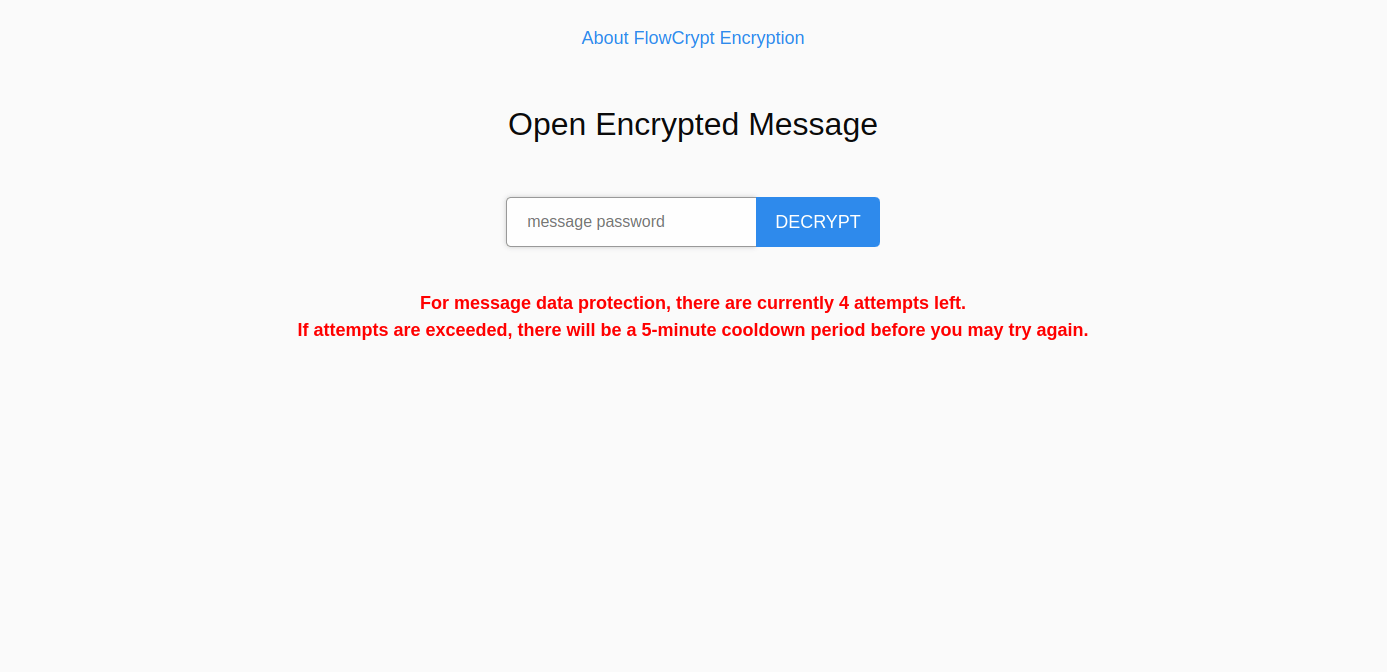
By default, users will have five attempts to input the correct password provided by the sender of the email:
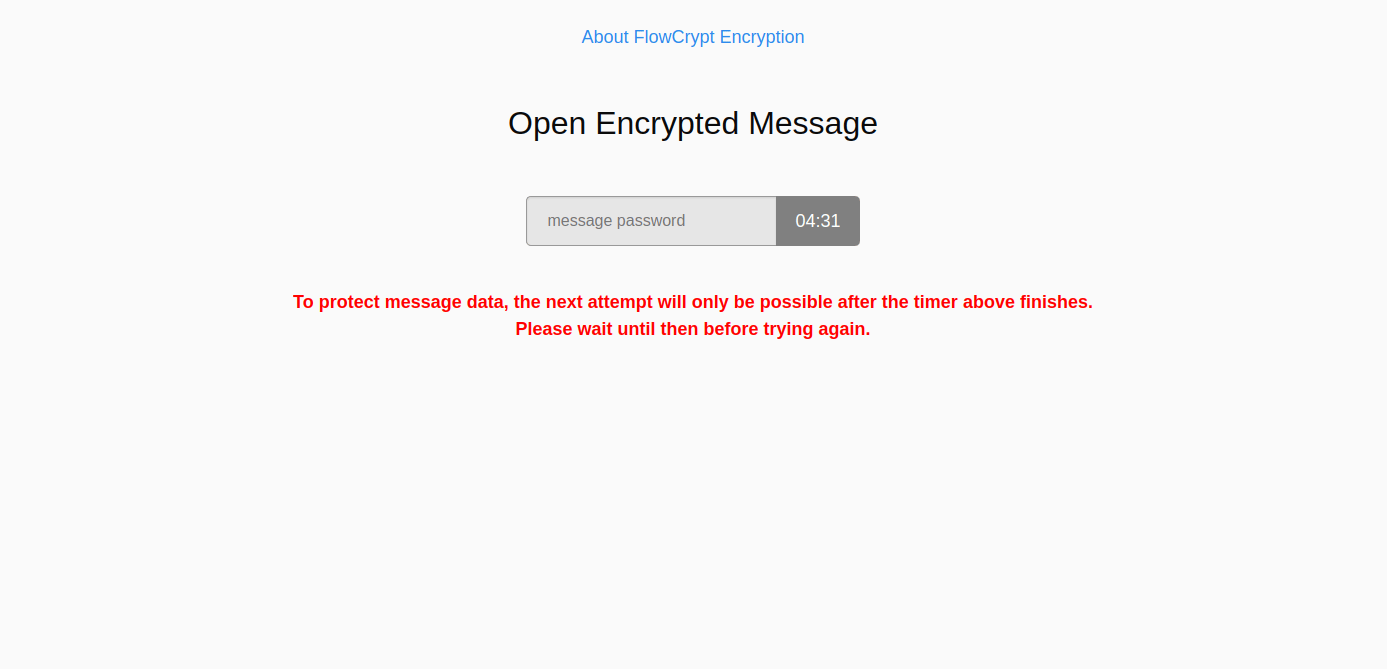
If all attempts are incorrect, the system will activate a security cooldown period of five minutes until the user can input the password again:
You can set your own values for the number of attempts and cooldown period using the web.portal.wrong.password.attempts.before.timeout and web.portal.wrong.password.timeout.seconds properties mentioned in the previous section.